Technology ❯Cybersecurity ❯Encryption
Backdoors Secure Transfer Protocols Telecommunications Apple Government Regulations Backdoor Vulnerabilities End-to-End Encryption User Privacy Secure Enclave Privacy
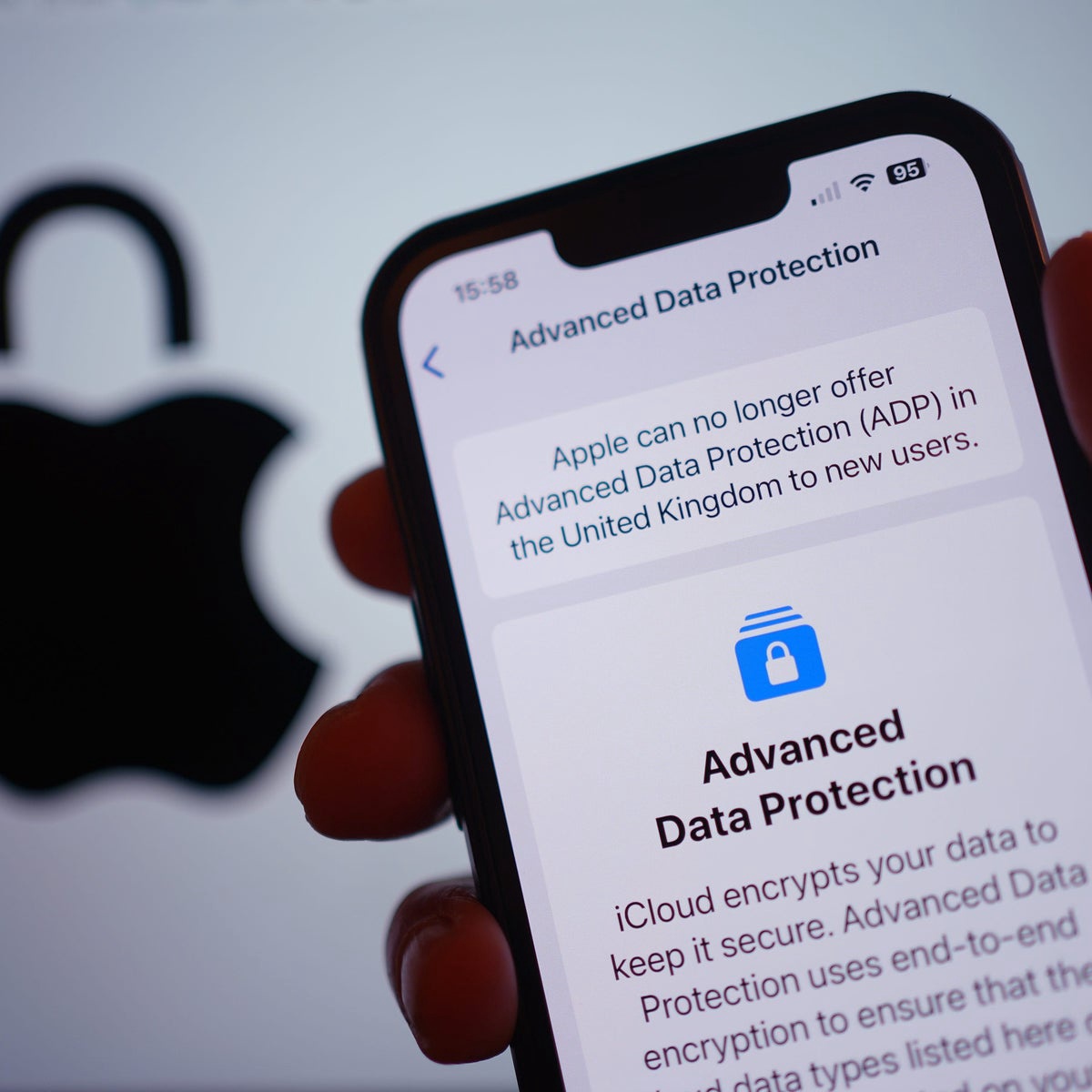
Apple challenges a secret UK directive to weaken encryption, with activists and media pushing for public hearings on the implications for global privacy and security.


