Data Breaches Cybersecurity Hacking Data Protection Phishing Cybercrime Crisis Management Email Services Cybersecurity Data Breaches

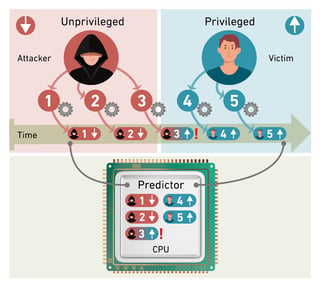
Coinbase confirms cooperation with U.S. and international law enforcement after hackers stole limited customer data and demanded a $20M ransom.