Hacking Hacking Fraud Malware Data Breaches Cyber Warfare Urban Infrastructure Data Protection User-Generated Content Viral Content

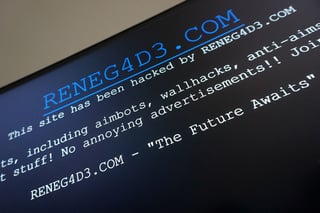
The Justice Department expands its RICO case against a cybercrime ring accused of stealing millions in crypto and financing lavish lifestyles.