Threats Vulnerabilities Software Vulnerabilities Updates Malware Operating Systems Ransomware Data Protection Web Browsers Cybersecurity

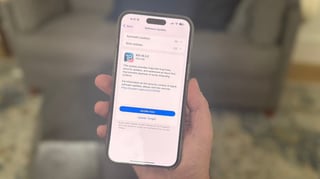
A new security update addresses CVE-2025-4664, a vulnerability actively exploited in the wild, requiring immediate user action to ensure protection.